In case you haven’t been keeping up with the big security news released in the past few days, there is a new and very dangerous vulnerability, known as “Follina” and captured in the CVE, CVE-2022-30190. It is definitely a vulnerability that you need to pay attention to and remediate according to Microsoft’s current guidance. In this post, I have written up a quick PowerShell script to remediate the vulnerability. Let’s take a look at how to automate Follina Vulnerability workaround with PowerShell.
What is the Follina Vulnerability?
With the Follina vulnerability, an attacker can use the Microsoft Support Diagnostic Tool (MSDT) in Windows to exploit and take over an affected victim’s machine. What is also dangerous about this vulnerability is that it is already being exploited in the wild.
The Microsoft Support Diagnostic Tool (MSDT) contains a remote code execution vulnerability that can be called using the URL protocol from an Office application like Word. By doing this, the attacker can then run arbitrary code with the privileges of the application. This allows the attacker to install programs, view, change, or delete data, create new accounts, and install malware, trojans, crypto miners, and even ransomware.
It essentially allows an attacker to use a malicious phishing email to coerce an unsuspecting end-user to download and open an affected Office document. Rather than using malicious macros as has historically been the case, an attacker can instead leverage the MSDT tool called from a Word document and, again, call all kinds of arbitrary code, commands, scripts, move laterally, etc.
What is Microsoft Support and Diagnostic Tool (MSDT)?
Microsoft Support Diagnostic Tool (MSDT) is a service that exists in Windows clients (11/10/8.1/7) and Windows Server operating systems. The tool allows for creating and analyzing diagnostic data and finding a resolution for the problems experienced by users.
Workaround guidance from Microsoft
The current guidance from Microsoft is found here:
Basically, the guidance contains two aspects that are mentioned from the Microsoft perspective:
- Disable MSDT URL Protocol
- Make sure you have the Windows Defender
The PowerShell script that I have quickly written up, should help to automate the process of remediating the MSDT URL Protocol, as you will see below. On the front of Windows Defender, note the following from Microsoft from the guidance page linked above.
Customers with Microsoft Defender Antivirus should turn on cloud-delivered protection and automatic sample submission. These capabilities use artificial intelligence and machine learning to quickly identify and stop new and unknown threats.
Customers of Microsoft Defender for Endpoint can enable attack surface reduction rule “BlockOfficeCreateProcessRule” that blocks Office apps from creating child processes. Creating malicious child processes is a common malware strategy. For more information see Attack surface reduction rules overview.
Automate Follina Vulnerability Workaround with PowerShell
Now, to the process to automate Follina vulnerability workaround with PowerShell. The steps to remediate the workaround involve:
- Checking for the MSDT URL Protocol registry key
- Backing up the registry key so this can be restored if desired in the future
- Deleting the registry key
You can perform these steps manually by checking for the MSDT registry key, which exists here:
- HKEY_CLASSES_ROOT\ms-msdt
The PowerShell code essentially automates the steps listed above, with the appropriate prompts for the end-user, such as “do you want to remediate, what file name do you want to use.” You can also take out the user prompts if you want the script to be fully automated.
# Script to check for the existence of the MSDT Protocol URL registry key and disable it
# Official Microsoft guidance here: https://msrc-blog.microsoft.com/2022/05/30/guidance-for-cve-2022-30190-microsoft-support-diagnostic-tool-vulnerability/
# It backs up the MSDT registry key and deletes the key
# Brandon Lee - v1.0
try {
Write-Host "Checking the system to see if the MSDT URL Protocol is still enabled" -ForegroundColor Yellow
New-PSDrive -Name HKCR -PSProvider Registry -Root HKEY_CLASSES_ROOT
$regkeypath = 'HKCR:\ms-msdt'
$check = (Get-ItemProperty $regkeypath)
if ($check -ne $null) {
try {
Write-Warning "Your machine is vulnerable to the Follina vunerability CVE-2022-30190. Would you like to disable MSDT URL Protocol and backup the registry key?" -WarningAction Inquire
$filepath = Read-Host -Prompt "Enter your file path where you want to backup the registry key. If you don't enter anything, it will default to backing up to your desktop"
if ([string]::IsNullOrWhiteSpace($filepath))
{
$filepath = "$($env:UserProfile)\Desktop\msdturlprotocol.reg"
}
reg export HKEY_CLASSES_ROOT\ms-msdt $filepath
reg delete HKEY_CLASSES_ROOT\ms-msdt /f
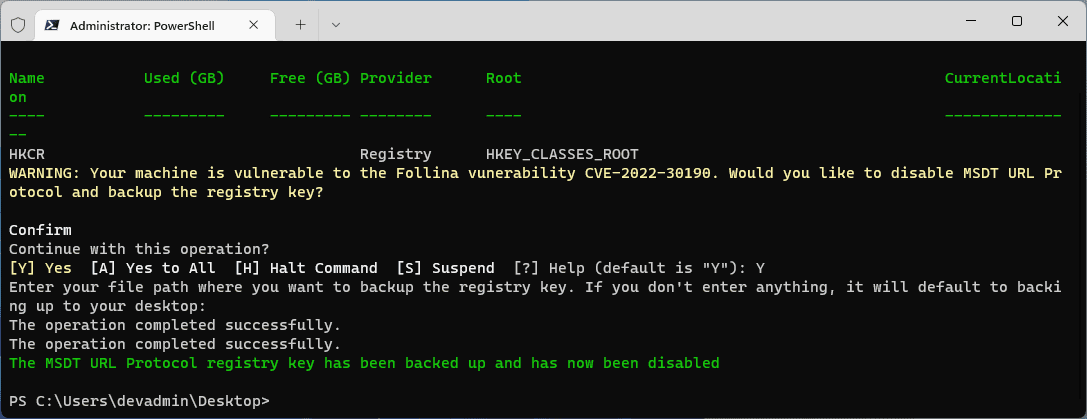
Write-Host "The MSDT URL Protocol registry key has been backed up and has now been disabled" -ForegroundColor Green
}
catch {
Write-Host "You chose not to implement the MSDT URL Protocol workaround" -ForegroundColor Red
}
}
else {
Write-Host "Your workstation already has the MSDT URL Protocol workaround" -ForegroundColor Green
}
}
catch {
Write-Host "Error running the script" -ForegroundColor Red
}Below is what it looks like to run the script.
After hitting Y, you will see the backup file created, and the registry key will be deleted from the machine.
Automate Follina Vulnerability Workaround with PowerShell
- What is the Follina vulnerability? The Follina vulnerability takes advantage of a zero-day vulnerability in the Microsoft Support Diagnostic Tool (MSDT). It allows an attacker to run arbitrary code on the client’s machine using an Office document opened by the end-user.
- What is Microsoft Support Diagnostic Tool (MSDT)? Microsoft Support Diagnostic Tool (MSDT) is a service that exists in Windows clients (11/10/8.1/7) and Windows Server operating systems. The tool allows for creating and analyzing diagnostic data and finding a resolution for the problems experienced by users.
- Why automate the Follina vulnerability workaround? Automating the Follina vulnerability workaround ensures it is performed uniformly and effectively and that steps are not missed. Using PowerShell is an easy way to automate performing the steps recommended by Microsoft.
Video showing the PowerShell Follina Patch script
Wrapping Up
The Follina vulnerability is a dangerous one in that it is a zero-day with only workarounds available at this time. It is never a good thing for attackers to be able to run arbitrary code on an end-user workstation with little effort. Hopefully, this post and PowerShell code will help you automate Follina vulnerability workaround with PowerShell.


0 Comments