Remote access is one of the most powerful tools in the toolbelt of an IT admin or helpdesk technician as it allows an IT worker to remotely access, configure, and administrate systems, regardless of whether they are physically near the system. IT admins often use remote access protocols such as Remote Desktop Protocol (RDP) and Secure Shell Protocol (SSH) to administer various remote servers and operating system hosts, including Windows Servers, clients, and Linux machines. Regarding RDP vs SSH, which is the better protocol to choose? What are the security challenges with each one? And regarding RDP vs SSH – which should you choose?
What is Remote Desktop Protocol (RDP)?
Remote Desktop Protocol (RDP) is a protocol developed by Microsoft allowing IT admins and other Windows users to connect to Windows devices remotely as if they are logging into the console. One end of the connection is the “RDP server,” or the machine hosting RDP services. The other end of the connection is the RDP client (mstsc.exe), which initiates the connection to the RDP server. It is sometimes referred to as Windows Remote Desktop Protocol.
Although meant for Microsoft Windows devices, RDP clients exist for other operating systems, including Linux, and mobile apps for iOS and Android. Historically the standard server port for the Remote Desktop Protocol server is TCP port 3389.
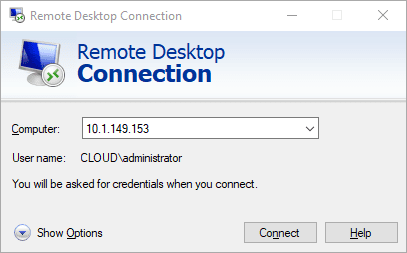
One of the huge advantages of Remote Desktop Protocol connections is they provide a full GUI solution for accessing Windows endpoints. PowerShell aside, Windows is not known for being friendly to being driven, configured, or managed using the command line only. Having RDP connections to Windows Servers and clients allows using the GUI of the target Windows host.
File copies and other features
Remote Desktop Protocol has many other capabilities built into the protocol, allowing many other features when connecting to remote Windows systems. With Remote Desktop Protocol, you can copy and paste files between your client and the target RDP host you are connecting to.
Additionally, you can redirect local printers, drives, ports, video capture devices, and other supported plug-and-play devices.
Common RDP architecture
Several architectures are seen in the wild, all the way from small environments, SMBs, all the way up to large enterprise organizations. Remote Desktop servers do not need any specialized infrastructure before you can connect to a server or workstation with an RDP connection. You can simply enable RDP on the target server or workstation and you can connect as long as you have TCP port 3389 open through a firewall.
There is a much more secure way to access Remote Desktop Protocol-enabled servers. The architecture used for the much more secure architecture uses a Remote Desktop Gateway (RDGW) server. The RD Gateway provides an RDP tunnel over SSL using a signed certificate. Clients configure their client RDP connections with the address of the RD Gateway server and their connection is tunneled through to the RDP target.
Otherwise, you can use a virtual private network VPN to access Remote Destop Protocol servers securely, without exposing them to the Internet.
Security vulnerabilities
Remote Desktop Protocol is not a protocol you want to place out on the perimeter of your network or exposed to the Internet without protection. Attackers commonly look for exposed Remote Desktop Protocol (RDP) servers out on the Internet. They will often attempt to brute force RDP servers to find weak passwords on an account that is granted access to the server.
It is amazing to see. If you place an RDP server out on the Internet, you will start to see nefarious login attempts within minutes. It is not so much the RDP protocol that is weak. Rather, the account passwords associated with the servers make them vulnerable. Often, organizations do not design their RDP infrastructure correctly and will place RDP servers on the Internet with no RD Gateway server in front. Logging and visibility to failed password attempts are generally overlooked.
Take a look at Microsoft’s guide to Remote Desktop Services architecture here:
How can you make RDP more secure?
We have already touched on this subject, but let’s speak to this specifically. Using an RD Gateway tunnel is the best practice architecture for connecting to Remote Desktop Protocol (RDP) servers. In this way, connections are secured, and you are not exposing TCP 3389 to the Internet, which is a bad decision.
If you choose to stick an RDP server out on the Internet (which is bad in many ways but can be done), you need to consider implementing multi-factor authentication on all accounts used. Multi-factor authentication MFA should not be optional on an exposed RDP server. It should be mandatory.
Also, think about implementing solutions that block IP addresses based on failed logins. Much like a “fail2ban” type solution, it will block access to IPs performing brute force attacks. There are many of these solutions out on the Internet, some for free, and others are pay-for products. Also, you can look for open source solutions that use technologies like PowerShell to perform similar functionality.
What is Secure Shell Protocol (SSH)?
Another very common remote access protocol is Secure Shell (SSH). What is Secure Shell? Secure Shell Protocol (SSH) is a very popular secure access protocol allowing administrators to access applications and hosts over insecure networks. It is commonly used for remote command line activities. Historically, we generally think about SSH connections being made to Linux targets or other devices such as network devices or appliances.
SSH was designed to replace insecure protocols like Telnet which communicate over the network in “clear text.” There is no GUI that you get with SSH. It is designed for command-driven secure access and does not offer GUI capabilities to users. One of the great things about SSH is it is built into any Linux distro you want to use and is readily available for access.
File copies
One of the capabilities provided by SSH is the ability to copy files using SCP. It provides a robust way to get files from one place to another without additional ports being open or needed to perform file transfers.
What is OpenSSH?
OpenSSH is a very common, open source implementation of the SSH protocol today. OpenSSH encrypts all traffic, so it is a secure way to securely access network resources and hosts, helping to eliminate eavesdropping.
Is SSH just for Linux?
One common misconception about SSH is that it is only available for Linux. However, OpenSSH Client and Server are both available for Windows Server and Client. You can install OpenSSH Server with the following PowerShell cmdlet oneliner:
Add-WindowsCapability -Online -Name OpenSSH.Server~~~~0.0.1.0You can also install the OpenSSH client using the GUI:
OpenSSH Server provides a great way to access Windows remotely. When running commands against remote Windows Servers, OpenSSH is a great way to access Windows securely.
Check out my posts on installing OpenSSH Server in Windows 10 and enabling public key authentication:
- OpenSSH Server Windows 10 Install with Public Key authentication – Virtualization Howto
SSH Security
One of the great things about SSH is it has strong security built into the protocol and standard. Unlike RDP, SSH can use a public and private key pair for server authentication. In other words, you can upload the public side of your key pair to the SSH server for a user. Then when the user connects, they present the private side of the key pair, which validates the connection for the user.
Security Vulnerabilities
SSH can have vulnerabilities from time to time. Admins need to keep up with patches and other updates to help remediate vulnerabilities associated with SSH. SSH, like RDP, can also be vulnerable to brute force attacks if exposed to the outside world.
You can take advantage of services such as application firewalls that can ban IPs attempting brute force attacks on SSH servers. SSH connections are much more secure using public key authentication. Use this if possible. It can also be secured with multi-factor authentication with third-party services such as Duo Security.
RDP vs SSH – Which should you choose?
Now that we have considered a few aspects of both RDP vs SSH, how do they compare? Which one should you choose? Using RDP and SSH are great ways to administer remote hosts. Often, as it is with any other answer in the world of IT – it depends. Both are tools that can do certain jobs and do those well.
First, if you need a graphical interface, it rules out SSH, since it is command-line only. Remote Desktop Protocol allows logging into and interacting with the GUI desktop session on a Windows Server or client. SSH is used for command line access to hosts and appliances of various sorts. But, as we mentioned, SSH can be used with Windows Servers and clients if you need to remote in and run command-line commands on the Windows target.
Arguably, SSH provides better security than RDP. RDP can easily be brute forced if it is on the perimeter. SSH can also be brute force attacked if it is only enabled with password authentication. However, it also can be enabled with public key authentication, which is much more secure. RDP does not have public key authentication and must be protected by other means, including using a Remote Desktop Gateway Server.
Multi-factor authentication should be required for RDP services, especially if you have an RDP server in the DMZ or perimeter without the protection of an RD Gateway Server.
RDP vs SSH FAQs
- What is Remote Desktop Protocol RDP? Remote Desktop Protocol RDP is a protocol for accessing Windows Servers and clients remotely. It provides a graphical interface for users and allows using the GUI as they would if they were at the console. The RDP client is built into the Windows operating system and the RDP Server is also built-in.
- What is Secure Shell Protocol SSH? Secure Shell Protocol SSH is a common protocol for accessing Linux servers, but it also can be used with Windows Server and client operating systems to access their command line or PowerShell remotely. It provides many great security benefits, such as public key authentication.
- Which should you choose – RDP vs SSH? For graphic user interface GUI interaction, you need to choose RDP. SSH is great for command line access and has many robust security capabilities built-in.
- RDP vs SSH, which is more secure? Side-by-side comparing RDP vs SSH, SSH is more secure than RDP since RDP cannot perform public key authentication. However, SSH can be just as dangerous if it is only secured with password authentication and exposed to the Internet. RDP can be secured effectively if architected correctly using an RD Gateway Server to proxy and tunnel the RDP connections.


0 Comments