RunZero, formerly known as Rumble, is a great new asset inventory and network discovery tool. It provides highly accurate asset identification and has become an excellent tool for security teams and IT administrators. This post will delve into the features that make runZero stand out, its versatility across multiple operating systems, and its effectiveness in client networks.
Why asset inventory and network discovery are needed
It is essential to have an accurate asset inventory of your environment for lifecycle management and security. Without an idea and visibility of what is on your network, it is easy to have “blind spots” that can harbor security vulnerabilities and other dangers for your environment.
There are many freemium solutions out there. However, you may be looking for alternatives to the simple IP scanners you have used over the years – think Angry IP, etc. While these tools are great for what they are, you may need something more fully featured.
What is runZero?
runZero is a product developed by HD Moore, a well-known figure in “hacking” and security tools. One of the key selling points of runZero is its asset inventory capabilities, allowing you to discover everything on your network. The data gathered by the platform provides a detailed and accurate representation of an organization’s hardware platforms and devices.
This information is invaluable for IT administrators as they can easily track unmanaged assets and ensure the security of their infrastructure. runZero makes this work amazing and simple, helping you to track your assets in an online database that can be accessed from anywhere.
With network discovery, you can search the network for assets and devices you may not know are connected, including wireless networks.
Multiple Operating Systems Compatibility
runZero supports multiple operating systems, making it a versatile solution for organizations with diverse IT environments. The platform can scan and identify devices running Windows, macOS, Linux, and various network devices, ensuring a comprehensive view of an organization’s assets.
Multiple Scan Schedules and Continuous Monitoring
With runZero, you can set up multiple scan schedules, allowing for a customized asset inventory and network discovery approach. This feature enables organizations to adapt their vulnerability management program according to their needs and ensure no stone is left unturned.
Rumble Network Discovery Transformed
runZero has built upon the foundation of Rumble Network Discovery, taking the concept to new heights. The platform can now provide additional information on assets, such as OS versions, services, etc. The data is presented in an easy-to-read format, making it simple for security teams to analyze and act upon.
Ensuring Security and Compliance with runZero
An effective vulnerability management program is crucial in today’s fast-paced digital world. runZero’s asset inventory and network discovery capabilities empower organizations to proactively address potential security risks and maintain compliance with industry standards.
Identifying Unmanaged Assets
Unmanaged assets pose a significant security risk as malicious actors can easily exploit them. runZero’s extremely accurate asset identification allows security teams to pinpoint these devices, take appropriate action, and minimize the potential attack surface.
Integration with Vulnerability Management Programs
runZero can easily be integrated with existing vulnerability management programs, enhancing the effectiveness of security measures and providing valuable insights into the organization’s security posture.
User Experience and Customer Support
runZero has received overwhelmingly positive feedback from users who have praised its ease of deployment, the accuracy of scan results, and the platform’s ability to work seamlessly across multiple operating systems. Users have also commended the responsive and knowledgeable customer support team.
Beta Testing and Continuous Improvement
runZero’s development team is committed to continuous improvement, as evidenced by their dedication to beta testing and addressing user feedback. While some users have reported minor complaints during the beta testing phase, the team has quickly addressed these concerns and ensured a top-quality experience for all users.
Installing runZero
Let’s look at the process to install runZero and get up and running with asset inventory and network scanning in your environment. runZero is a SaaS-based management plane with a SaaS console fed by what runZero refers to as an explorer. The explore is the on-premises software you run to collect information about assets and your network. You can think of these as agents that collect data about your network and deliver the information to the SaaS console.
You can sign up for runZero free for 20 days and run without limitation. When you sign up, runZero will walk you through the steps you need to complete to get up and running with network scans, which is great. It doesn’t leave you guessing.
System requirements
Below, you can see the minimum requirements for the explorer component:
Processor running at 2.0Ghz or faster
At least 4GiB of memory (1GiB available)
At least 16 GiB of memory (8GiB for small environments)
Windows Server 2012R2, Windows 10 Build 1604, or newer
Administrator access
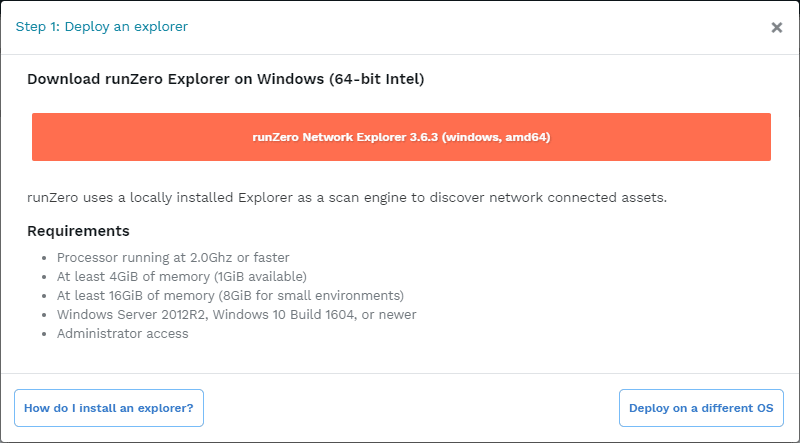
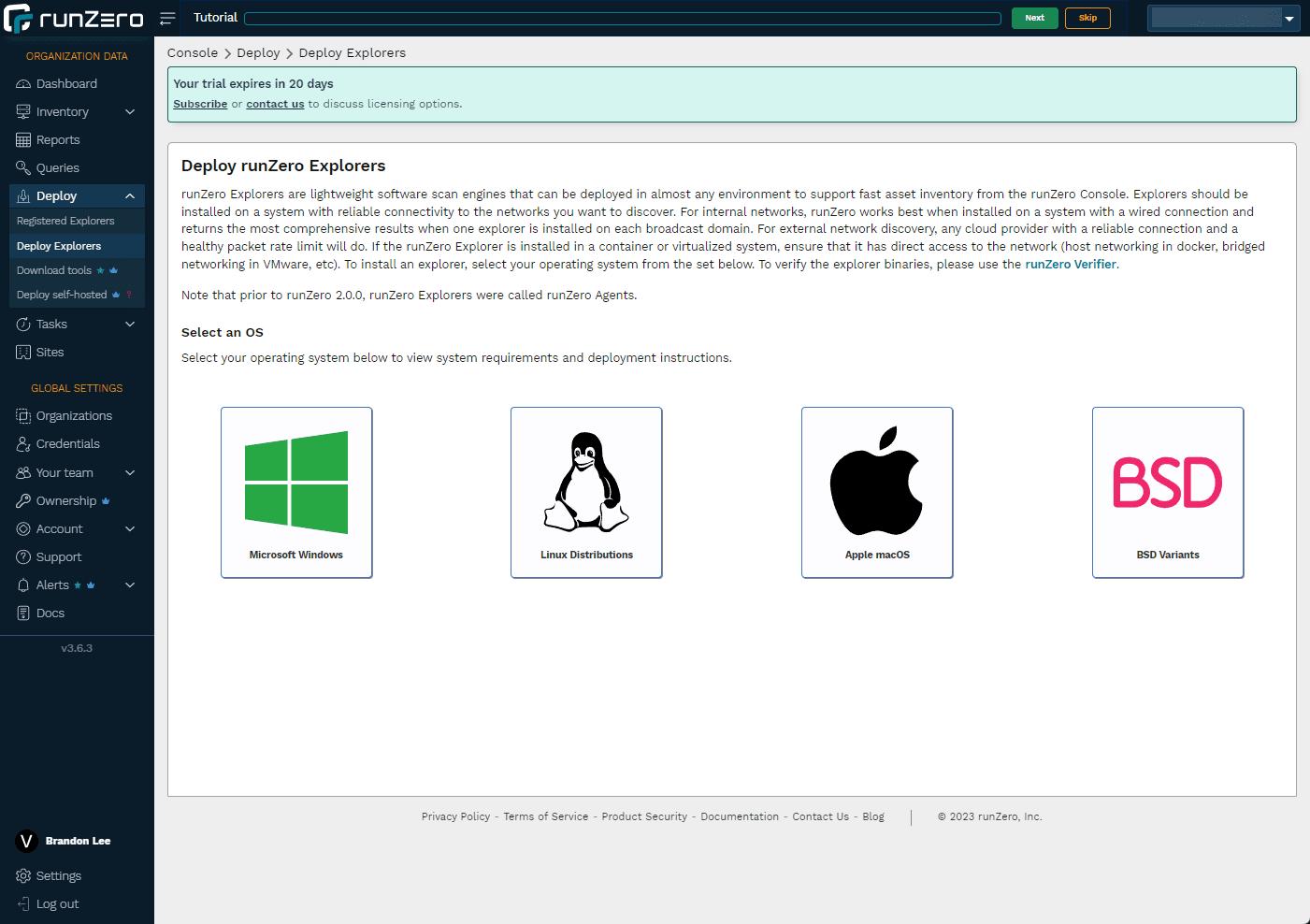
Supported operating systems
The screenshot above details the Windows installation. However, runZero can be installed on a wide variety of operating systems. As you can see below, you can install on Windows, Linux, Apple, and BSD.
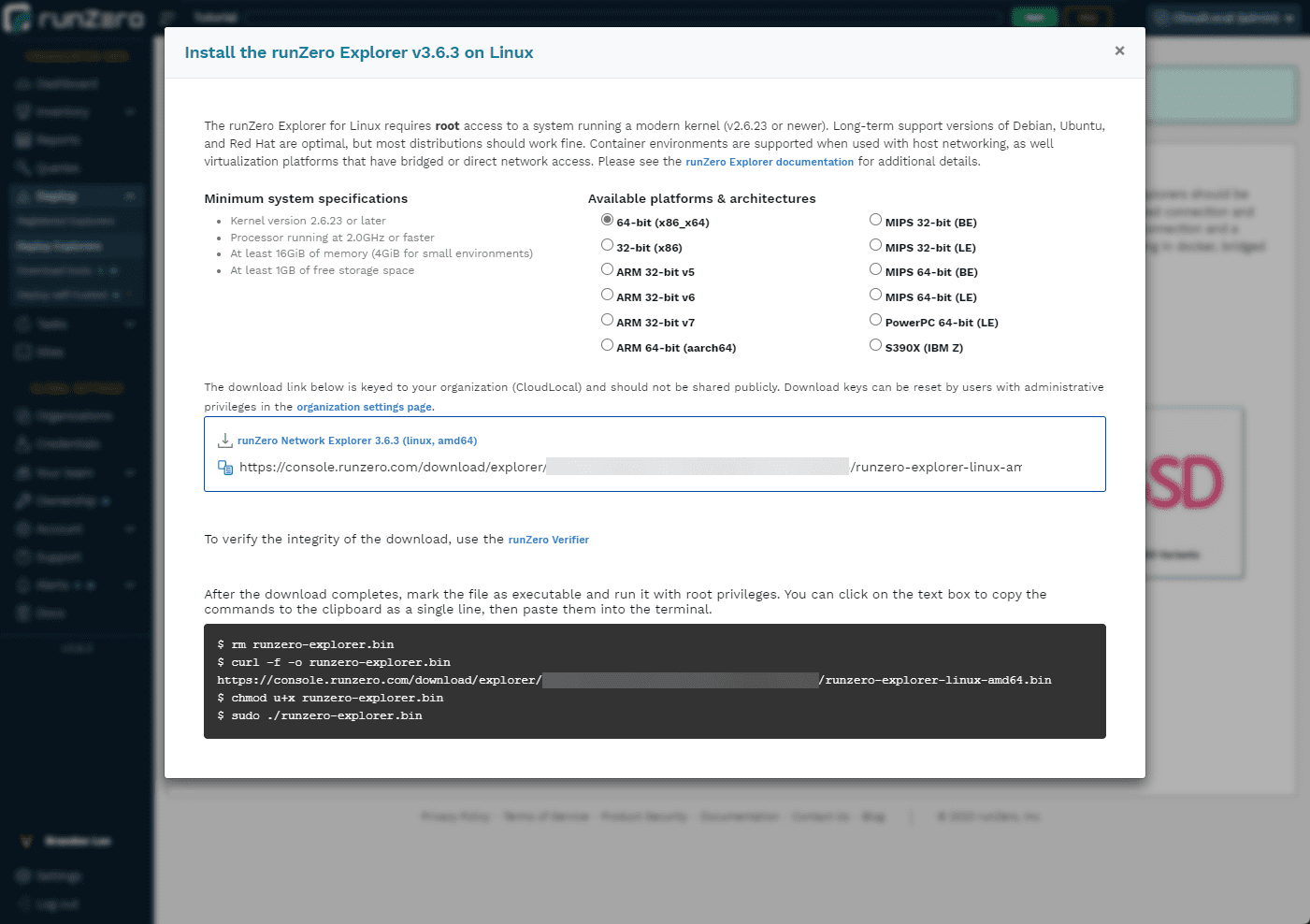
Below are details for the Linux installation.
Container support
I was a bit dismayed when I didn’t see containers listed on the main installation page. If I could say it, this was the only grip I had with the installation. But, it is a minor complaint overall. However, it appears containers are supported, but do require you to build your own container from a Docker file: Installing an Explorer (runzero.com)
It would be great to see an official Docker container created an maintained in the future for this purpose as this would be an extremely efficient way to deploy the explorers across many environments. Below are instructions to deploy it in a container.
To generate a suitable identifier, the openssl tool may be used:
$ openssl rand -hex 16
01b0283809b24511929d0b062bd36109
Here is a sample Containerfile you can edit and use:
#
# Sample Containerfile for running the runZero Explorer in a container, with
# screenshot support.
#
FROM debian:stable-slim
WORKDIR /opt/rumble
# Ensure curl is available and install tools for wireless scanning.
#
RUN apt update && apt install -y curl wireless-tools
# Install Chrome for screenshots.
#
RUN curl -o chrome.deb https://dl.google.com/linux/direct/google-chrome-stable_current_amd64.deb &&
apt install -y ./chrome.deb
# Set AGENT_URL to be the download URL for your Linux runZero Explorer. To
# find your URL, go to https://console.runzero.com/deploy/download/explorers
# and click on the first URL box to copy it to the clipboard.
#
ENV AGENT_URL=https://console.runzero.com/download/explorer/DT[uniqueToken]/[versionID]/runzero-explorer-linux-amd64.bin
# This ID is used to track the Explorer even if the container is rebuilt.
# Set it to a unique 32 character hex ID. You can generate one via:
#
# $ openssl rand -hex 16
#
ENV RUMBLE_AGENT_HOST_ID=[UNIQUE-ID]
# If you need to set environment variables to change the Explorer behavior,
# you can do so via the ENV directive. Example:
#
# ENV RUMBLE_AGENT_LOG_DEBUG=true
ADD ${AGENT_URL} runzero-explorer.bin
RUN chmod +x runzero-explorer.bin
# For full functionality the runZero scanner needs to send and receive raw
# packets, which requires elevated privileges.
USER root
# The argument `manual` tells runZero not to look for SystemD or upstart.
ENTRYPOINT [ "/opt/rumble/runzero-explorer.bin", "manual" ]Installation on a traditional OS
After downloading the explorer for Windows, the installation is straightforward. You just execute the explorer. There is no wizard, etc.
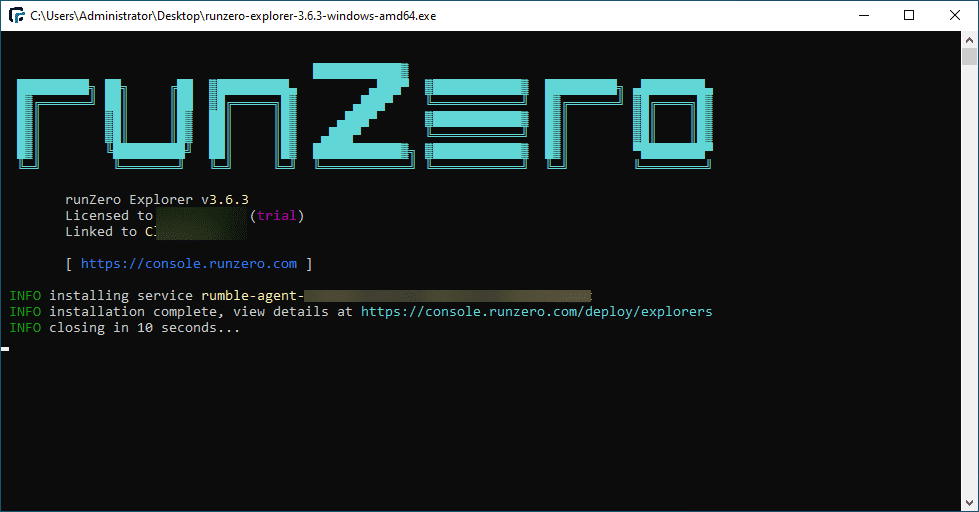
Running Scans
After installing your explorer in the environment, you can execute a scan from your explorer. With the scans, you can define the parameters, with which subnets you want to scan, descriptions for these, templates to use, SNMP, credentials, etc. So, lots of options for discovery.
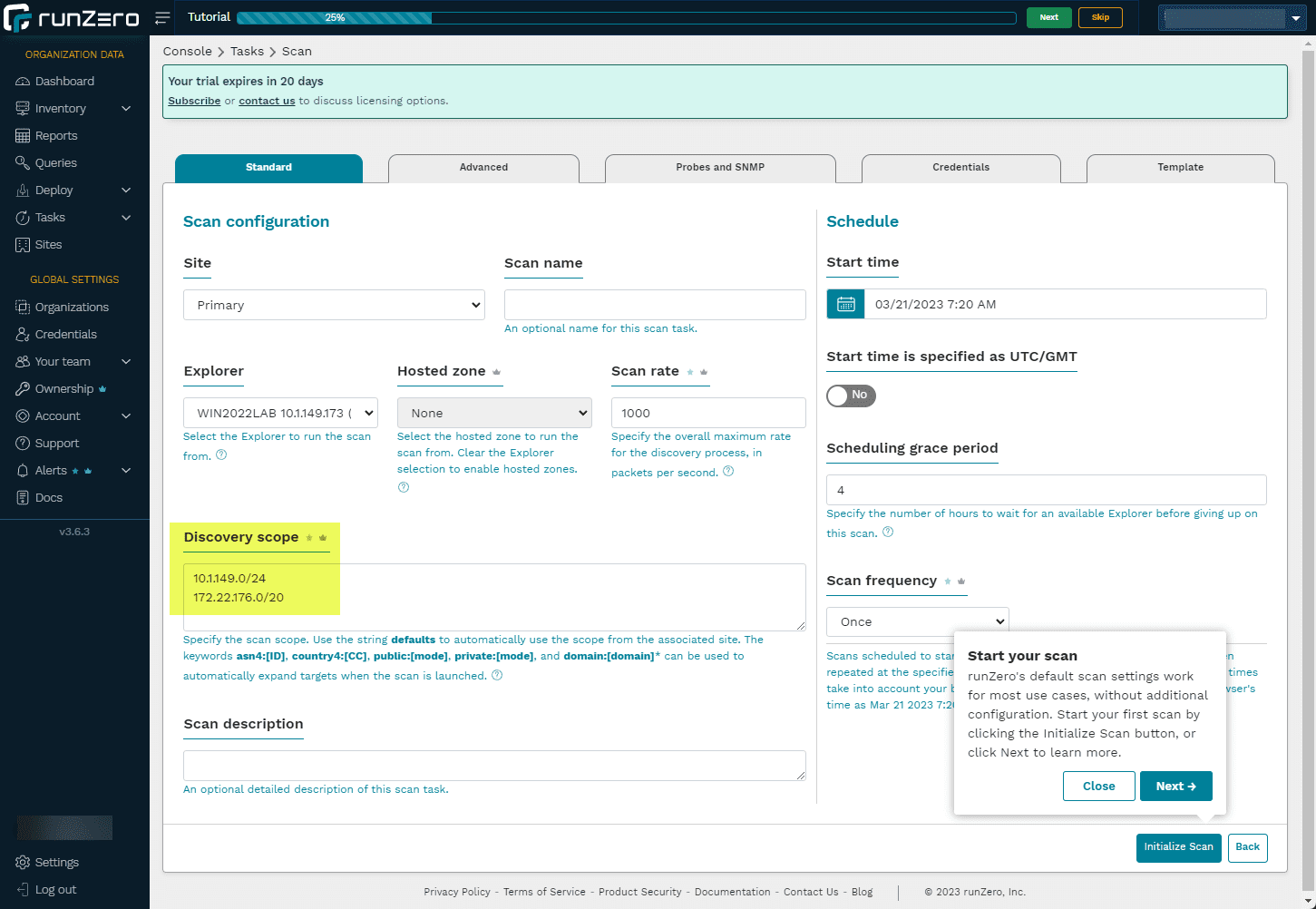
Confirm the subnets you want to scan.
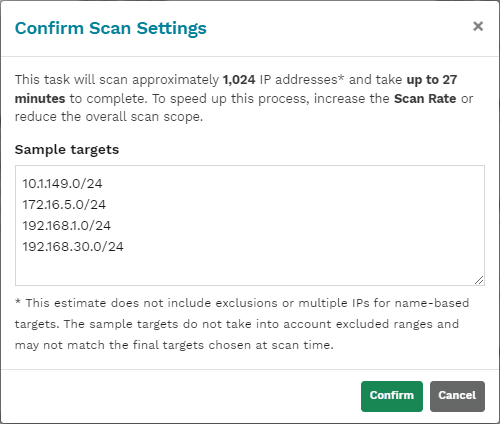
Viewing the scan results
Below, you can see the level of detail you get with scan results. I like how runZero details the devices and visually shows devices with multiple IP addresses. You get a wealth of information for each device that you can drill into
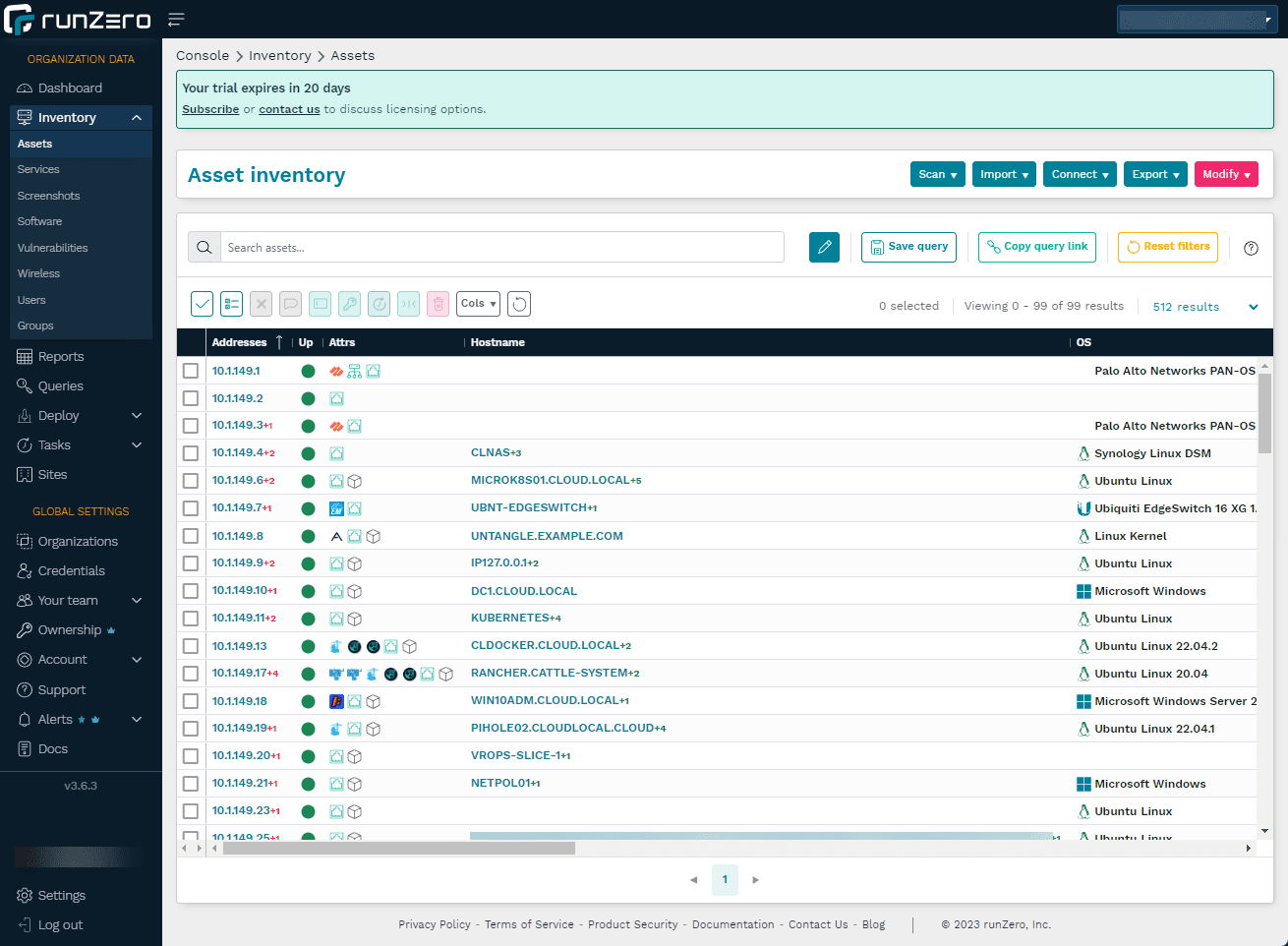
You get reports on all kinds of attributes associated with the device.
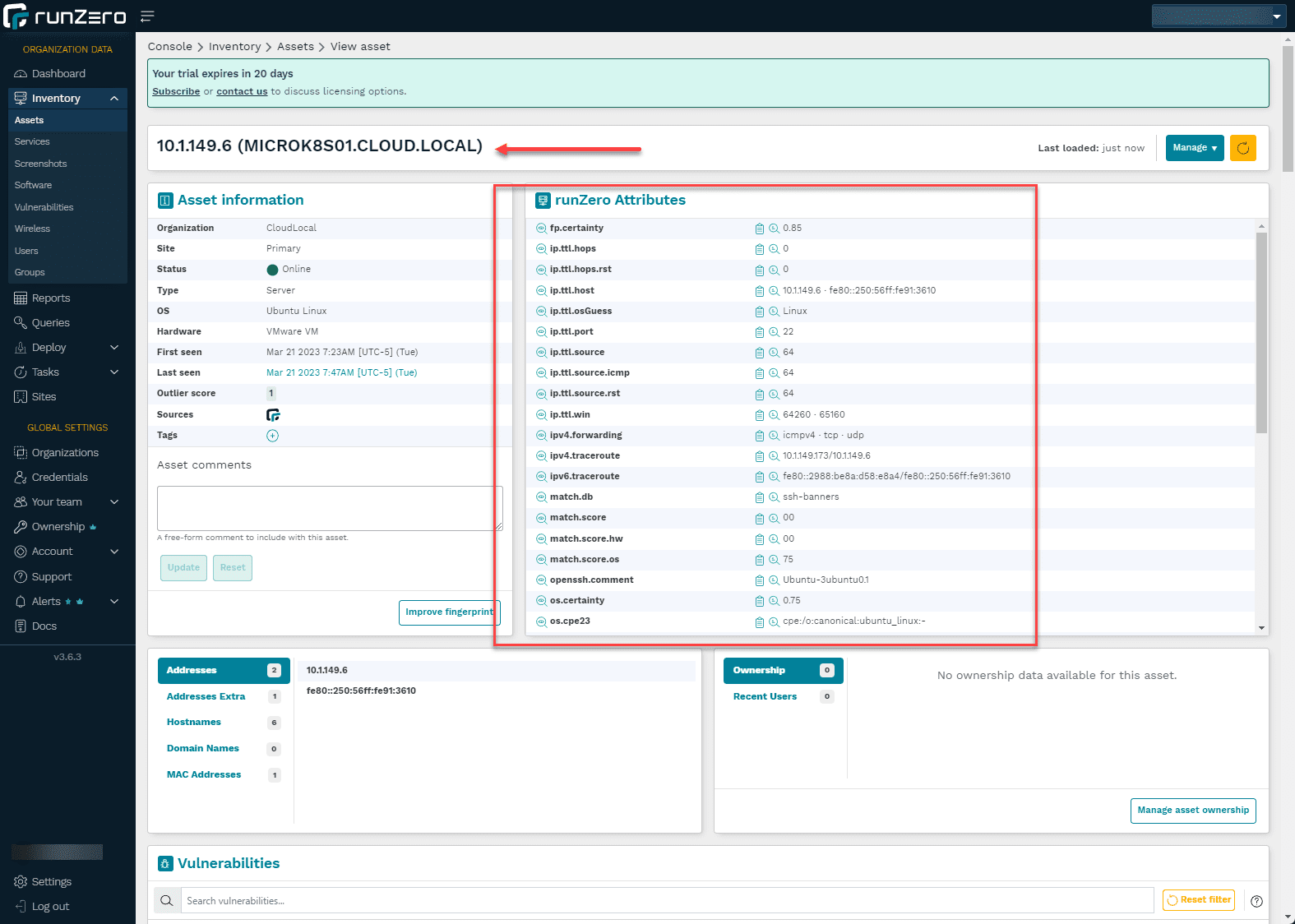
Software report for the device.
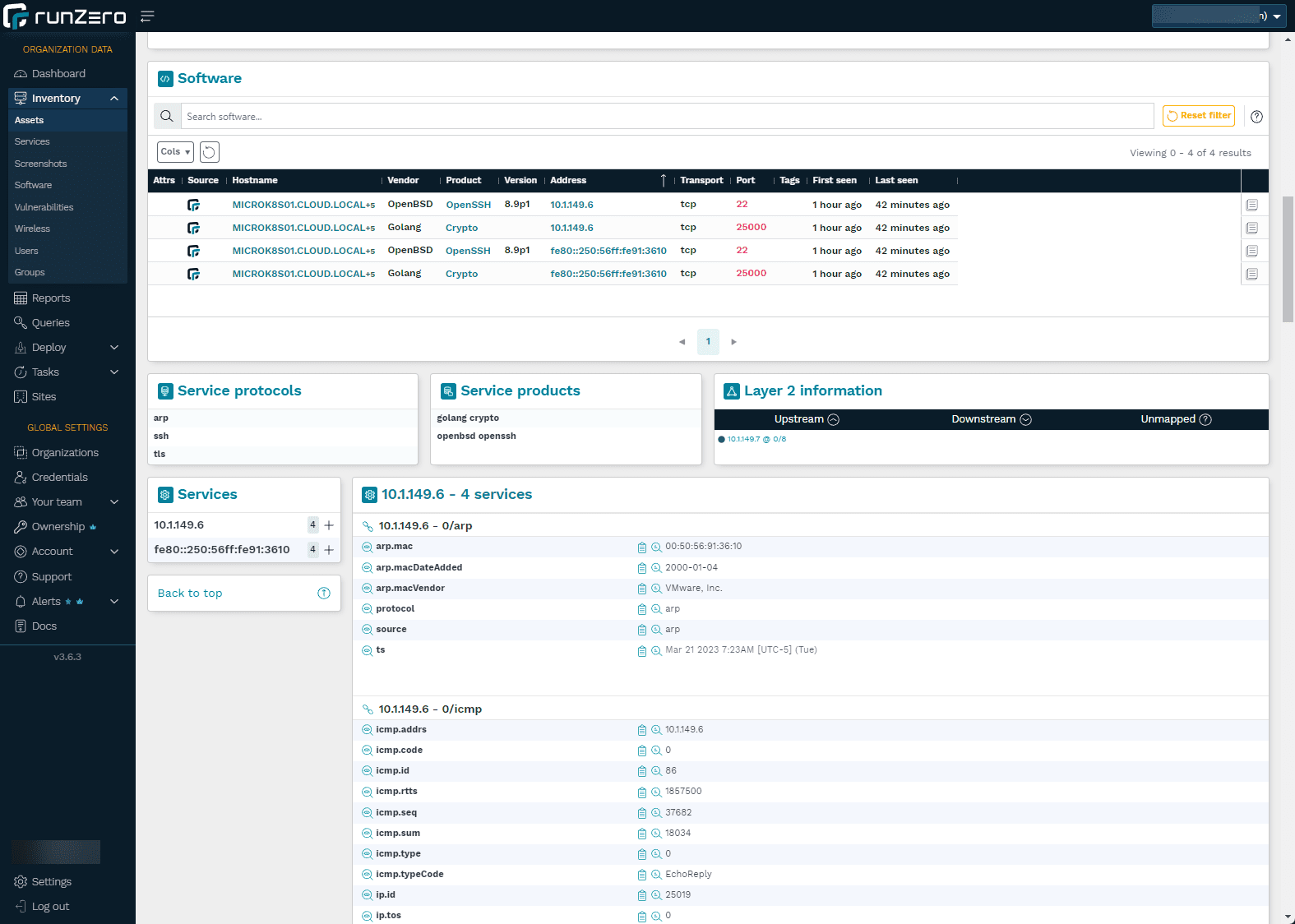
Reporting
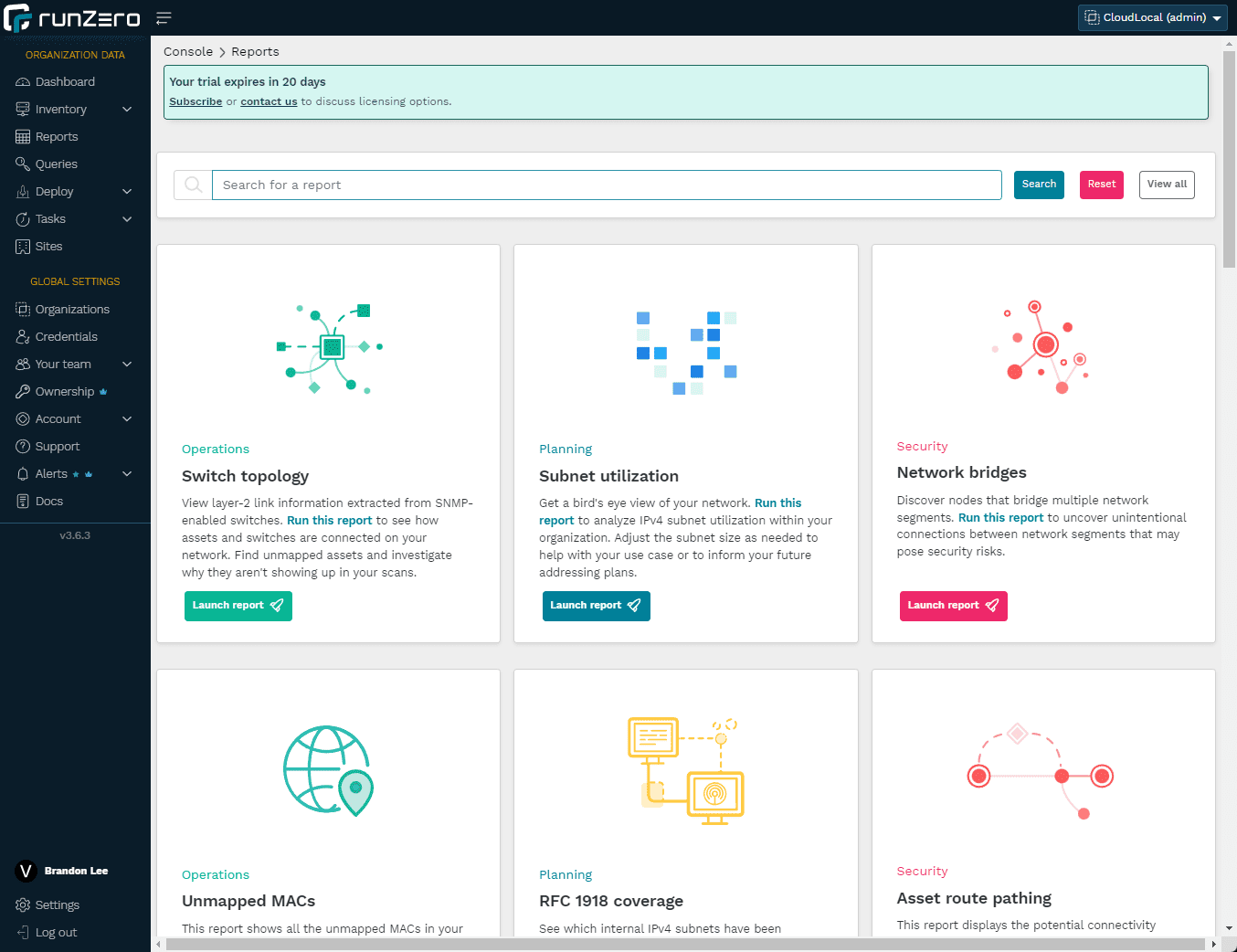
With all the information you collect with runZero, you have a great database from which you can run reports with intelligence that runZero provides. Note the reports you have access to:
Switch topology
Subnet utilization
Network bridges
Unmapped MACs
RFC 1918 coverage
Asset rout pathing
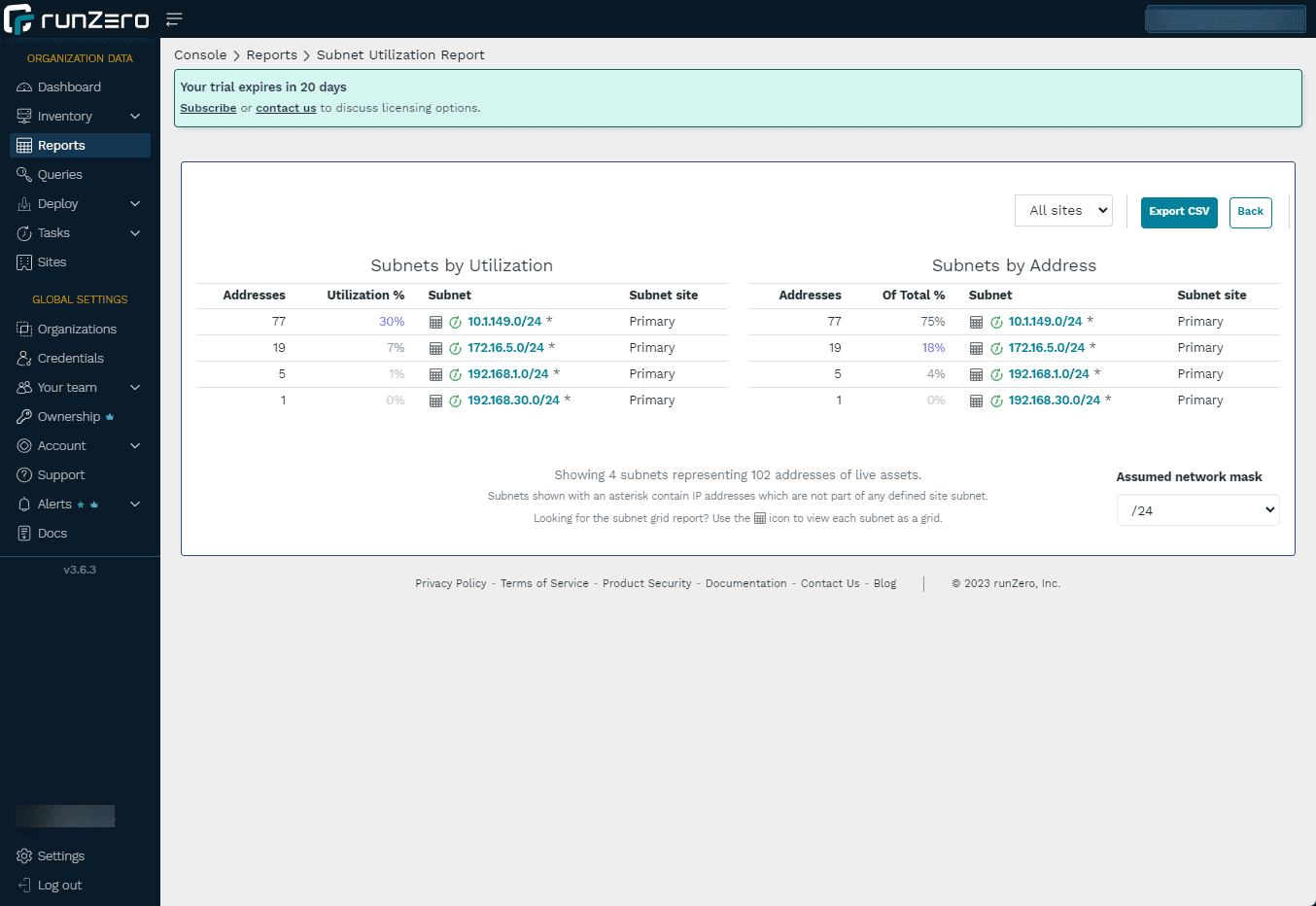
Below is the subnet utilization report, which is a great report if you want to know how much of a given subnet you are utilizing.
Looking to the Future
As runZero continues evolving, we can expect further enhancements to its impressive capabilities. The platform will likely expand its support for additional hardware platforms and operating systems and offer new features to help organizations better manage their assets and maintain a robust security posture.
Wrapping Up
I found runZero to be a great tool with many features and capabilities. It takes asset discovery and network inventory to the next level, providing IT admins and security researchers robust tools to discover and inventory the network. It will be great to see how the solution continues to evolve and grow as new features are added, etc. Check out runZero here: Asset inventory and network visibility solution | runZero.


0 Comments