
Managing and maintaining Active Directory (AD) in today’s enterprise environments is crucial to day-to-day operations. Active Directory Users and Computers (ADUC) is a central component of this management process with Active Directory Domain Services on-premises.
Let’s look at Active Directory Users and Computers, AD Domain Services, and the various tools and features available for managing users, computers, and other AD objects. Note, you will need to be a member of the domain admins group to manage and configure aspects of the Active Directory domain effectively.
Understanding Active Directory Users and Computers (ADUC)
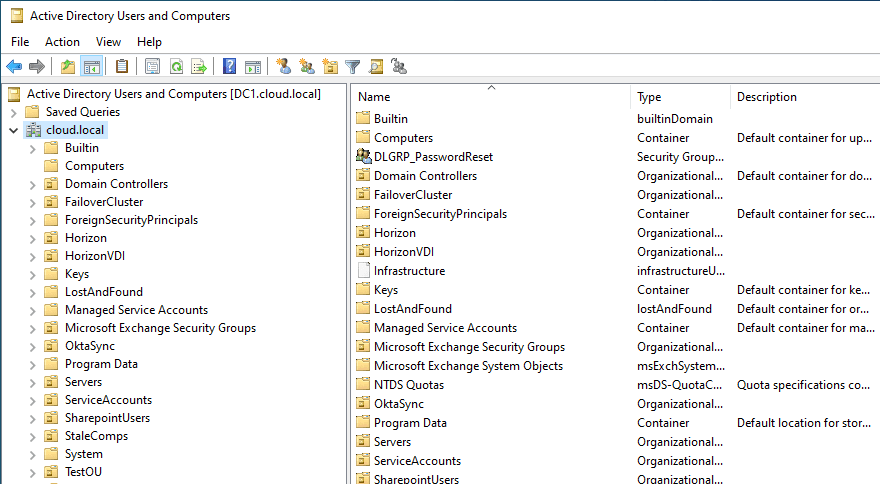
Active Directory Users and Computers is a Microsoft Management Console (MMC) snap-in that provides a graphical interface for managing Active Directory objects, including an Active Directory user account, member Windows servers, object properties, reset user accounts, etc.
With ADUC, administrators can manage Active Directory user accounts, computer accounts, groups, and organizational units (OUs) within an Active Directory domain.
Installing Active Directory Domain Services (AD DS) and Remote Server Administration Tools (RSAT)
Before accessing Active Directory Users and Computers, you must install Active Directory Domain Services on a Windows Server. This process involves adding the AD DS role through the Server Manager.
After installing AD DS, the next step is to install the Remote Server Administrator Tools (RSAT) on your workstation to manage Active Directory objects. RSAT does install Active Directory Users and Computers, Active Directory Administrative Center, AD DS tools, and lightweight directory tools (AD LDS).
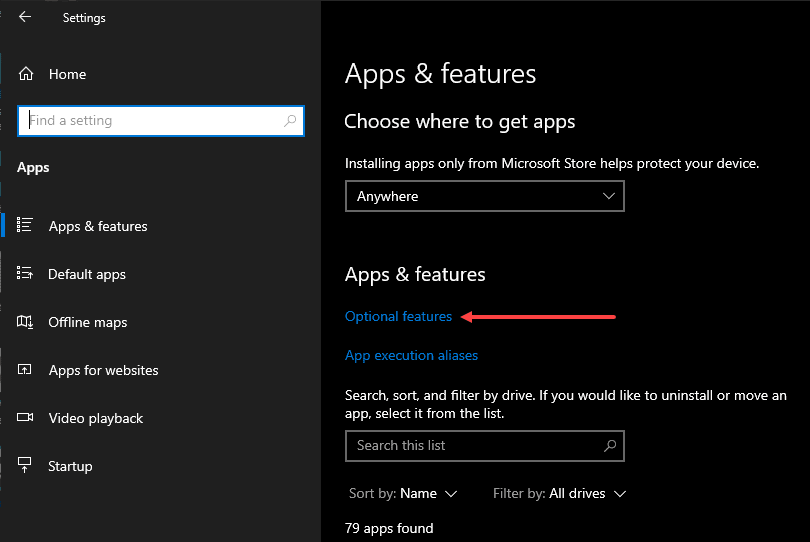
To install RSAT, press Windows key + I to navigate to settings. Under Apps & features, click Optional features to manage optional features in Windows 10 & 11.
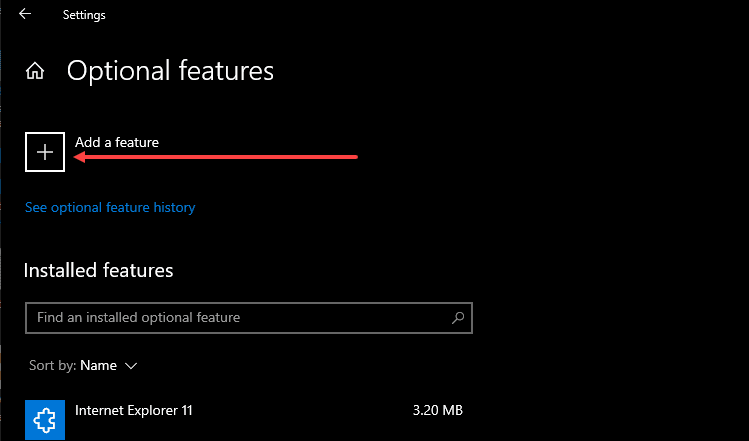
Click the + sign under Add a feature.
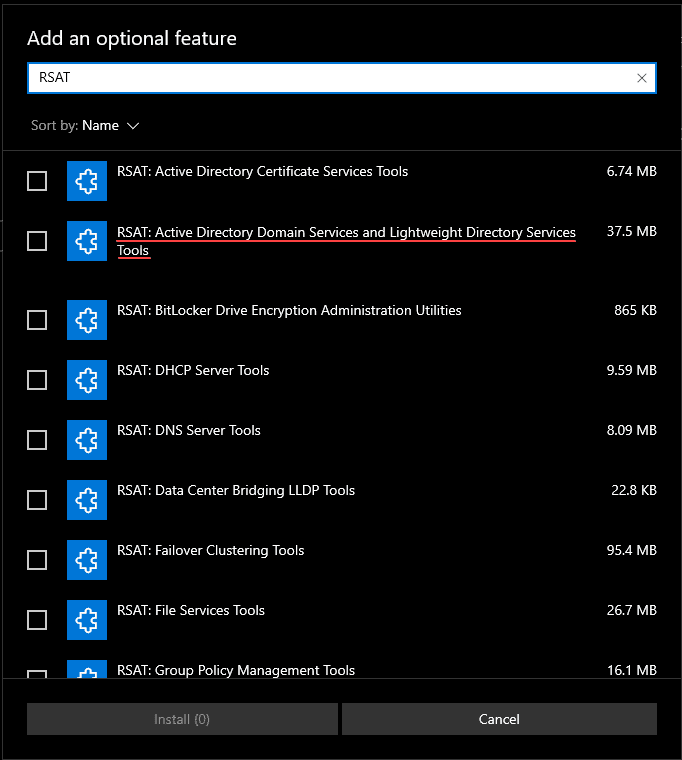
Type in “RSAT” in the search bar. You will see all the available RSAT modules for installation. For Active Directory Users and Computers, you will want to install RSAT: Active Directory Domain Services and Lightweight Directory Services Tools.
Accessing Active Directory Users and Computers
To open Active Directory Users and Computers, click the Start Menu, and navigate to “Windows Administrative Tools.” Locate “Active Directory Users and Computers” and click to open the console. Alternatively, you can launch ADUC by using the command dsa.msc from a run, command, or PowerShell prompt.
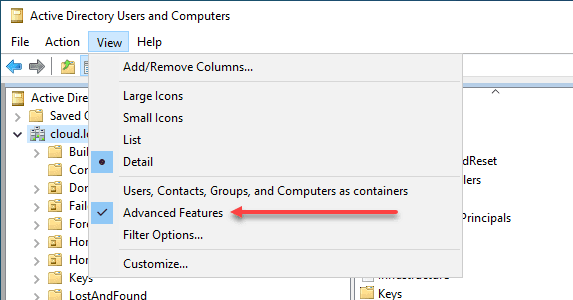
If you have enabled advanced features, you can access additional options by right-clicking on the domain name and selecting “Advanced Features.”
Managing User Accounts
User accounts in Active Directory allow users to log on to the domain and access resources. To create a new user account, right-click the OU where you want the account to reside, and select “New” followed by “User.”
Fill in the required information, such as the user’s full name and user logon name, and click “Next.” Set a password and configure the password settings, then click “Finish” to create the account.
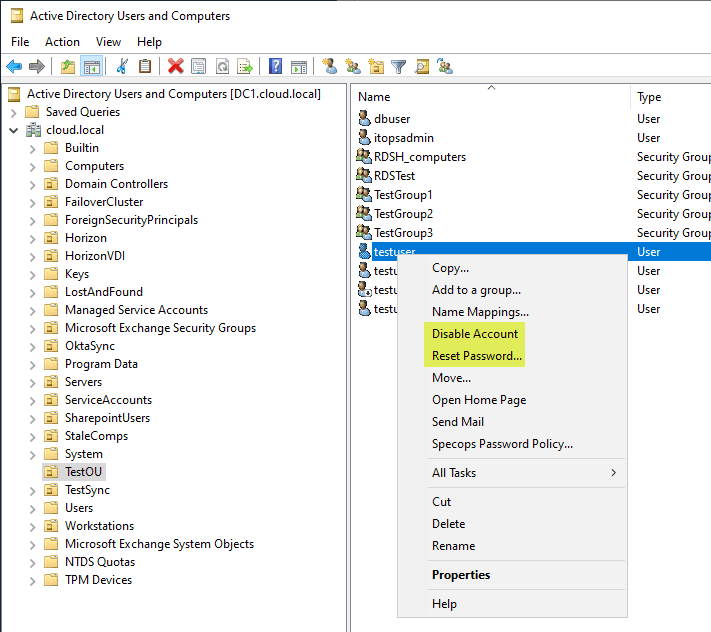
If you need to disable a user account, locate the account in the ADUC console, right-click the user object, and select “Disable Account.” To reset a user account password, right-click the account and choose “Reset Password.”
Managing Computer Accounts
Each computer in an Active Directory domain has a corresponding computer account. These accounts help track and manage the computers within the domain. To create a new computer account, right-click the OU where the computer should reside, select “New,” and then choose “Computer.” Enter the computer’s name and click “OK.”
To reset a computer account password, right-click the computer object and select “Reset Account.” This process generates a new password for the computer account, which must be synchronized with the computer’s local password.
Organizing Active Directory Objects with Organizational Units (OUs)
Organizational Units are container objects within AD that help administrators manage and organize Active Directory objects in Active Directory domains. OUs can contain users, computers, groups, and even other OUs. By creating a structured hierarchy of OUs, you can streamline the process of managing your Active Directory domain.
Delegating Permissions and Managing Group Policy
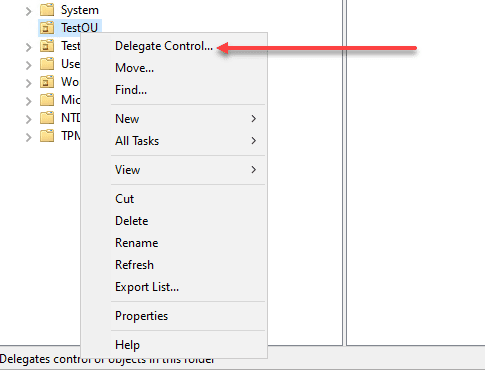
To delegate permissions to other administrators or users, right-click an OU or another AD object and select “Delegate Control.” Follow the wizard to assign specific permissions to the chosen user or group.
Group Policy allows administrators to define settings for users and computers within the domain. To create a new Group Policy object (GPO), right-click an OU, select “Create a GPO in this domain, and Link it here,” and give the GPO a name. You can then configure the settings within the Group Policy Management Console.
Working with Groups and Group Scopes
Groups in Active Directory help manage permissions and access to resources. There are three group scopes: domain local, global, and universal.
Domain local groups can contain users and groups from any domain within the forest, while global groups can only contain users and groups from their own domain. Universal groups can contain users and groups from any domain within the forest and are available for use in other domains.
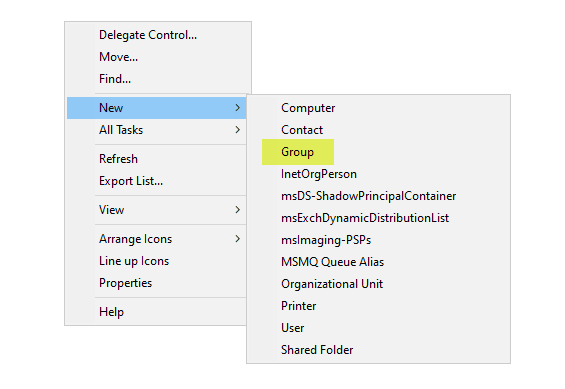
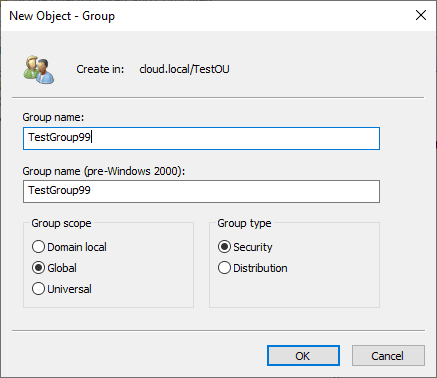
To create a new group, right-click the OU where the group should reside, select “New,” and then choose “Group.” Enter the group’s name, select the group scope, and click “OK.”
To add users to the group, double-click the group object, navigate to the “Members” tab, and click “Add.”
Securing Active Directory Objects
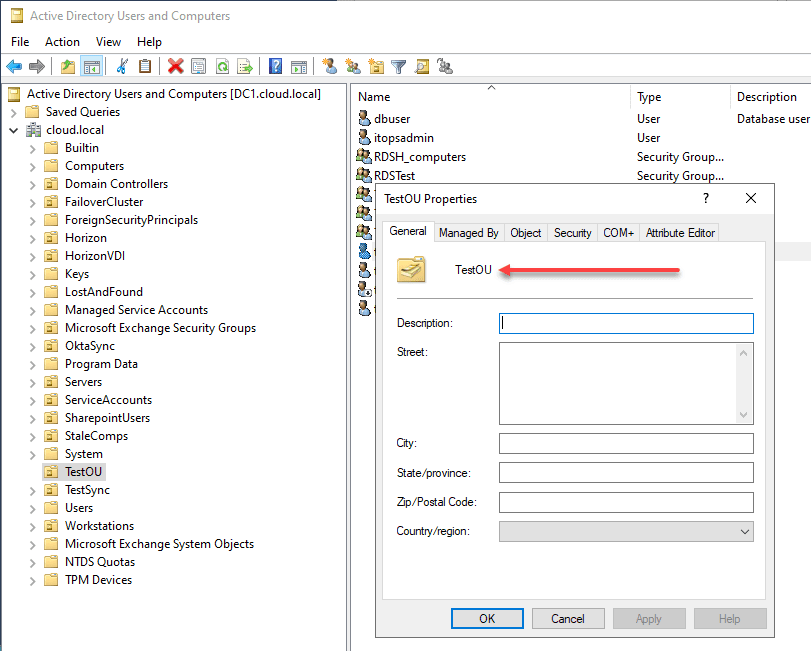
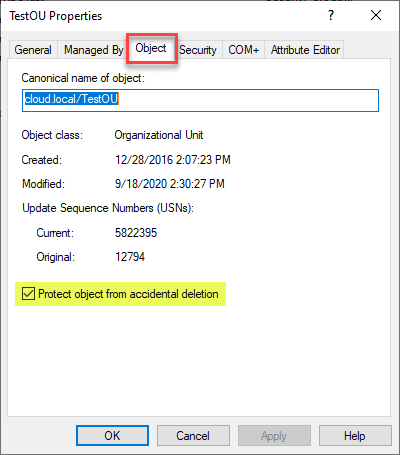
Protecting your Active Directory objects is essential for maintaining a secure environment. To secure an AD object, right-click the object and select “Properties.” Navigate to the “Object” tab and check the box for “Protect object from accidental deletion.” This option prevents the object from being deleted without proper authorization.
Enabling Advanced Features
To access advanced features within the ADUC console, click “View” in the menu bar and select “Advanced Features.” Enabling advanced features provides access to additional properties and settings for AD objects.
Streamlining Active Directory Management with AD Administrative Center
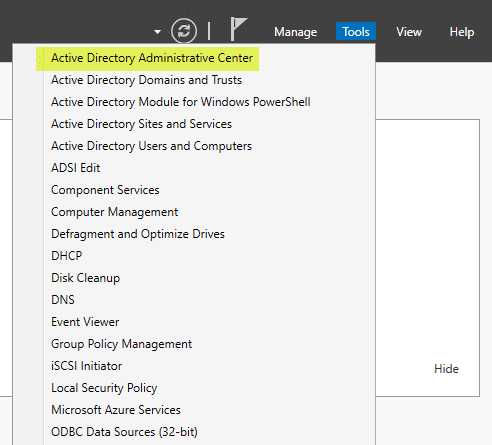
Active Directory Administrative Center is another management tool offering a more modern and intuitive interface than ADUC. It is designed to simplify managing AD objects and supports new AD features, such as the Active Directory Recycle Bin and Fine-Grained Password Policies. To access the Administrative Center, navigate to “Windows Administrative Tools” in the Start Menu and click on “Active Directory Administrative Center.”
Leveraging Lightweight Directory Services Tools (AD LDS)
Active Directory Lightweight Directory Services (AD LDS) is a directory service that provides a more flexible and scalable solution for specific directory service scenarios. AD LDS tools can be used with AD DS tools to manage directory-enabled applications. To install AD LDS tools, open the Control Panel, click on “Turn Windows features on or off,” and check the box for “Active Directory Lightweight Directory Services Tools.”
VMware Horizon is a common Enterprise solution that takes advantage of AD LDS directory services for Horizon Connection Server replication.
Understanding Active Directory Sites and Services
Active Directory Sites and Domain Controllers play a crucial role in optimizing network traffic and ensuring the availability of AD services. An AD site represents a physical location with a well-connected network, while domain controllers are servers that host the AD DS service. Managing sites and domain controllers involves configuring site links, subnets, and replication schedules to optimize AD performance across multiple locations.
Using Active Directory Tools for Role Administration
Role Administration Tools include various features that help administrators manage specific roles and services within an Active Directory environment. Examples of these tools include DNS Server Tools, DHCP Server Tools, and more. To install Role Administration Tools, navigate to the Control Panel, click on “Turn Windows features on or off,” and expand “Role Administration Tools” to select the desired features.
Exploring Active Directory Domain Services (AD DS) Features
Active Directory Domain Services (AD DS) is the foundation of an AD environment, offering various features to manage users, computers, and other resources.
Some of these features include Group Policy, which enables centralized management of settings; Trust Relationships, which facilitate resource sharing between domains and forests; and Global Catalog, which provides a searchable index of AD objects for faster queries.
Utilizing Active Directory Module for Windows PowerShell
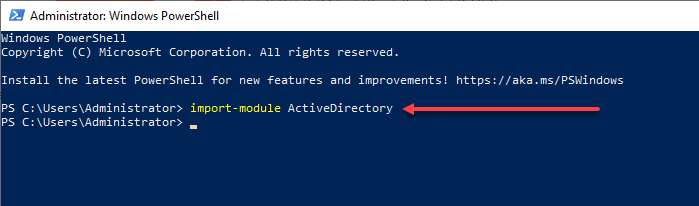
The Active Directory module for Windows PowerShell offers a command-line alternative to managing AD objects. With a comprehensive set of cmdlets, administrators can automate repetitive tasks and perform bulk operations on AD objects. To install the module, open Server Manager, click “Add Roles and Features,” and select the “Active Directory module for Windows PowerShell” feature.
Active Directory PowerShell commands
Import the Active Directory module:
Import-Module ActiveDirectoryCreate a new user account:
New-ADUser -Name "John Doe" -GivenName "John" -Surname "Doe" -SamAccountName "jdoe" -UserPrincipalName "jdoe@example.com" -Path "OU=Users,DC=example,DC=com" -AccountPassword (ConvertTo-SecureString "P@ssw0rd!" -AsPlainText -Force) -Enabled $trueCreate a new Organizational Unit (OU):
New-ADOrganizationalUnit -Name "Sales" -Path "DC=example,DC=com"Add a user to a group:
Add-ADGroupMember -Identity "Group Name" -Members "User Name"Disable a user account:
Disable-ADAccount -Identity "User Name"Get a list of all users in an OU:
Get-ADUser -Filter * -SearchBase "OU=Users,DC=example,DC=com"Move a user account to a different OU:
Move-ADObject -Identity "CN=User Name,OU=SourceOU,DC=example,DC=com" -TargetPath "OU=DestinationOU,DC=example,DC=com"Reset a user’s password:
Set-ADAccountPassword -Identity "User Name" -NewPassword (ConvertTo-SecureString "NewP@ssw0rd!" -AsPlainText -Force) -ResetFind all users with a specific attribute (e.g., title):
Get-ADUser -Filter 'Title -eq "Manager"' -Properties TitleModify an attribute for a user (e.g., phone number):
Set-ADUser -Identity "User Name" -OfficePhone "+1 (555) 123-4567"These examples demonstrate various tasks that administrators can perform using the Active Directory module for Windows PowerShell, allowing for efficient management of AD objects.
Monitoring and Troubleshooting Active Directory Performance
Active Directory performance is crucial for maintaining a stable and efficient network. Monitoring tools like Performance Monitor, Event Viewer, and Repadmin can help administrators track the health of their AD environment and identify potential issues. Regularly reviewing logs and performance metrics can aid in proactively addressing problems before they escalate.
Implementing Active Directory Security Best Practices
Securing your Active Directory environment is essential to protect sensitive data and ensure network integrity. Implementing security best practices includes maintaining up-to-date patches, enforcing strong password policies, regularly reviewing permissions and group memberships, and monitoring for signs of unauthorized access or suspicious activity.
Security recommendations
Securing your Active Directory environment is essential to protect sensitive data and ensure network integrity. Implementing security best practices includes the following recommendations:
Regularly update and patch systems: Keep your domain controllers and all systems in the network up-to-date with the latest security patches and updates to minimize vulnerabilities.
Enforce strong password policies: Implement password complexity requirements, minimum password length, and password history to prevent users from choosing weak or easily guessable passwords.
Implement account lockout policies: Configure account lockout settings to lock user accounts after a specified number of failed login attempts, helping prevent brute-force attacks.
Limit user privileges: Follow the principle of least privilege by granting users and groups the minimum required permissions to perform their tasks. Regularly review and adjust permissions as necessary.
Enable multi-factor authentication (MFA): Require MFA for administrative accounts to provide an additional layer of security beyond just a password.
Secure domain controllers: Protect domain controllers by placing them in a secure location, both physically and within the network, and by implementing security measures such as firewalls and intrusion detection systems.
Monitor and audit Active Directory activity: Regularly review event logs and configure audit policies to track changes in AD objects, group memberships, and permission assignments. Use tools like Event Viewer and third-party solutions to analyze logs and identify anomalies.
Implement Role-Based Access Control (RBAC): Define roles and assign permissions based on job responsibilities, ensuring that users have access only to the resources necessary for their role.
Maintain a secure backup and recovery plan: Regularly back up your Active Directory environment and test your recovery procedures to ensure you can quickly restore operations in case of an incident.
Train employees on security awareness: Educate users about the importance of security, including best practices for password management, recognizing phishing attempts, and reporting suspicious activity.
Regularly review group memberships: Periodically review and clean up group memberships to remove inactive users and ensure that only authorized personnel have access to sensitive resources.
Encrypt network traffic: Use technologies like IPsec, LDAPS, and Kerberos to encrypt communication between domain controllers and clients, as well as between domain controllers.
Frequently Asked Questions about Active Directory Management and Security
What is the difference between Active Directory Users and Computers (ADUC) and Active Directory Administrative Center (ADAC)?
Active Directory Users and Computers (ADUC) is a traditional management tool that provides a graphical user interface for managing Active Directory objects.
Active Directory Administrative Center (ADAC) is a newer tool that offers a more modern and intuitive interface, supporting new AD features like the Active Directory Recycle Bin and Fine-Grained Password Policies.
How can I use PowerShell to manage Active Directory?
You can use the Active Directory module for Windows PowerShell to manage AD objects. This module provides a comprehensive set of cmdlets for performing tasks such as creating users, modifying attributes, and managing group memberships.
What are Active Directory Lightweight Directory Services (AD LDS) tools?
Active Directory Lightweight Directory Services (AD LDS) tools are used for managing directory-enabled applications. AD LDS is a directory service that provides a more flexible and scalable solution for specific directory service scenarios, working in conjunction with AD DS tools.
How do I secure my Active Directory environment?
To secure your Active Directory environment, follow best practices such as keeping systems updated, enforcing strong password policies, limiting user privileges, implementing multi-factor authentication, monitoring and auditing AD activity, and training employees on security awareness.
What are some best practices for managing Active Directory group memberships and permissions?
Some best practices for managing group memberships and permissions in Active Directory include implementing Role-Based Access Control (RBAC), following the principle of least privilege, regularly reviewing group memberships, and monitoring changes in group memberships and permission assignments.
How can I monitor and troubleshoot Active Directory performance?
You can use monitoring tools like Performance Monitor, Event Viewer, and Repadmin to track the health of your AD environment and identify potential issues. Reviewing logs and performance metrics can help you proactively address problems before they escalate.
Wrapping up
The Microsoft Active Directory Users and Computers snap-in is integral to the enterprise data center and legacy Microsoft Active Directory Domain Services infrastructure. It is the centralized management tool used to manage and configure an organization’s Active Directory users and computers. Understanding how you can use it and the other tools found in the Remote Server administration tools is essential to manage your environment effectively.




0 Comments